Blog
Our Latest Insights
From warm-up tricks to deliverability hacks, our blog breaks down everything you need to know to land in the inbox and connect with your audience.
SPF, DKIM, and DMARC: The Complete Setup Guide for 2025

Email deliverability in 2025 isn’t just about writing compelling subject lines or engaging content. Behind the scenes, your domain’s authentication setup determines whether your carefully crafted emails land in the inbox or disappear into the spam folder abyss.
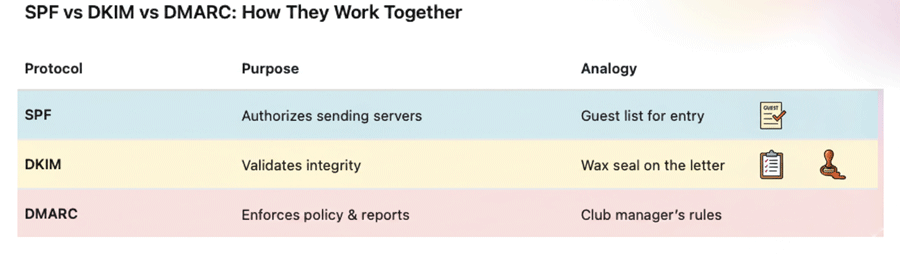
Three acronyms sit at the heart of this challenge: SPF, DKIM, and DMARC.
Think of them as the “three security locks” on your domain’s front door. Without them, spammers can impersonate you, ISPs will distrust you, and your inbox placement will suffer. With them, your brand looks professional, your emails get through, and your audience actually sees your message.
This complete guide will break down what each protocol does, why it matters in 2025, and how to set it up step by step — with practical examples, common mistakes to avoid, and testing tips.
Why Email Authentication Matters in 2025
Back in the early days of email marketing, basic “delivery” was enough. If your server could hand off a message, most inbox providers accepted it. Fast forward to 2025, and the landscape has completely changed.
-
AI-driven spam filters evaluate behavior, sender reputation, and authentication.
-
Phishing attacks have skyrocketed, forcing providers like Gmail and Outlook to demand stricter verification.
-
Brand trust is now visible in inboxes — with BIMI logos and authenticated senders getting higher credibility.
The bottom line: Without proper SPF, DKIM, and DMARC, even high-quality emails risk being quarantined, throttled, or rejected outright.
Email Deliverability vs. Delivery: What’s the Real Difference?
SPF: Sender Policy Framework
What is SPF?
SPF is like your domain’s guest list. It tells inbox providers which servers are allowed to send email on behalf of your domain.
Analogy: Imagine a nightclub with a bouncer. SPF is the guest list the bouncer checks before letting people in.
How it works
-
You publish an SPF record in your domain’s DNS.
-
When you send an email, the recipient’s server checks if the sending server’s IP matches that record.
-
If it matches → pass. If not → fail.
Example SPF record for Google Workspace
v=spf1 include:_spf.google.com ~all
Setup steps
-
Log in to your DNS provider (e.g., Cloudflare, GoDaddy).
-
Add a TXT record containing your SPF policy.
-
Test by sending to Gmail and checking the email header for spf=pass.
Common mistakes
-
Publishing multiple SPF records (you should only have one).
-
Forgetting to update SPF after adding a new sending service.

DKIM: DomainKeys Identified Mail
What is DKIM?
DKIM adds a digital signature to each outgoing email, proving that it hasn’t been altered in transit.
Analogy: Think of DKIM as a wax seal on a letter — if the seal is intact, the recipient knows it’s genuine.
How it works
-
Your sending server uses a private key to sign each email.
-
The recipient’s server checks this against the public key published in your DNS.
-
If they match → the email passes integrity checks.
Setup steps
-
Generate DKIM keys in your email provider (e.g., Google Workspace, Microsoft 365, Zoho).
-
Publish the public key as a DNS TXT record.
-
Ensure your ESP is signing all outbound mail with the private key.
-
Send a test message and check for dkim=pass in the header.
Common mistakes
-
Misconfigured selectors (leading to alignment failures).
-
Forgetting to rotate keys periodically.

DMARC: Domain-based Message Authentication, Reporting & Conformance
What is DMARC?
DMARC acts as the rulebook that tells inbox providers what to do when SPF or DKIM fails. It also provides reporting, so you can see who’s trying to spoof your domain.
Analogy: Imagine DMARC as the manager who instructs the nightclub bouncer: “If someone’s not on the guest list or their seal is broken, send them home or put them under watch.”
How it works
-
You set a DMARC policy in DNS: none, quarantine, or reject.
-
Providers follow your instructions when SPF/DKIM fail.
-
Reports (RUA, RUF) show which IPs are sending on your behalf.

Example DMARC record
v=DMARC1; p=quarantine; rua=mailto:
This email address is being protected from spambots. You need JavaScript enabled to view it. ; ruf=mailto:This email address is being protected from spambots. You need JavaScript enabled to view it. ; fo=1
Setup steps
-
Start with p=none (monitoring only).
-
Analyze reports to ensure legitimate traffic is aligned.
-
Move to quarantine → suspicious mail goes to spam.
-
Finally, enforce reject for maximum protection.
Common mistakes
-
Jumping straight to reject without monitoring.
-
Not setting up reporting addresses (you lose visibility).
Together, they form a layered defense system. Without all three, your email security and deliverability remain incomplete.
How to Test & Monitor Authentication
-
Send test emails to Gmail or Outlook.
-
Look for: spf=pass, dkim=pass, dmarc=pass.
-
-
Use tools like:
-
MXToolbox
-
Leverage Zharik’s Deliverability Insights to track inbox placement, not just delivery.
10 Common Reasons Emails Go to Spam (2025 Guide to Inbox Placement)
Common Mistakes & How to Avoid Them
-
Using multiple SPF records instead of one consolidated record.
-
Forgetting to update records when switching ESPs.
-
Setting DMARC to reject too early.
-
Not rotating DKIM keys.
FAQs
Do I really need all three?
Yes. SPF and DKIM handle technical checks, but DMARC enforces policy and reporting.
Will BIMI work without DMARC?
No. BIMI requires DMARC with enforcement (quarantine or reject).
How long does DNS propagation take?
Usually a few minutes to 48 hours, depending on your provider.
What happens if I only set SPF?
You’re partially protected, but spoofers can still bypass you without DKIM/DMARC.
Conclusion
SPF, DKIM, and DMARC aren’t just technical acronyms — they’re the foundation of trustworthy email marketing in 2025.
By setting them up correctly, you:
-
Protect your brand from spoofing.
-
Improve your inbox placement rates.
-
Build trust with ISPs and subscribers.
At Zharik, we go beyond authentication. With domain warm-up, inbox monitoring, and deliverability insights, we help you not just deliver emails — but deliver them to the inbox.
We offer the best services for our customer


